Activities
More PQC at Google
date: 2025.09.09
Last year, we launched the Post-Quantum Cryptography Hub, a collection of resources and updates on Google’s quantum-safe journey. It’s designed to share our approach to this massive cryptographic migration.
My contributions are often for CISOs and senior leaders figuring out where to begin. These articles reflect real conversations about how to get buy-in for this unique program.
Here are a few of my posts you’ll find on the hub:
- Perspectives on Security for the Board: Navigating the Quantum Leap: A high-level piece based on discussions with senior stakeholders and board members.
- Cloud CISO Perspectives - Getting ready for Quantum: This one was heavily edited by marketing, but the core message is still there.
- From Inventory to Agility: A CISO’s Guide to Robust Key Management: This one shares Google’s perspective on crypto inventory and crypto agility - ie the capability to tackle not just this but also the migration that comes after that. We see an inventory not as a compliance exercise, but as a way to solve today’s most critical problems, like proper key management. The inventory then becomes a valuable side effect of a better security process.
Post-Quantum Cryptography at Google
date: 2022.07.11
I got a friendly acknowledgement in a Google Blog post for my contribution to the NIST competition as part of the Classic McEliece team.
How Google is preparing for a post-quantum world
Conferences
date: 2021.08.15
I actively contributed to the organization and / or program committees [PCs] of the following events:
- Selected Areas in Cryptography (SAC) 2021 ‒ Virtual Conference ‒ Sep 29 - Oct 1, 2021 [PC member].
- Latincrypt 2021 ‒ Virtual Conference ‒ October 6-8, 2021 [PC member].
- Selected Areas in Cryptography (SAC) 2020 ‒ Virtual Conference ‒ Oct 19-23, 2020 [PC member].
- WEWoRC 2015 ‒ Cottbus, Germany, October 2015 [PC member]. (Update: workshop canceled)
- Indocrypt 2014 ‒ New Delhi, India, December 2014 [PC member].
- Selected Areas in Cryptography (SAC) 2014 ‒ Montreal, QC, Canada, August 2014 [PC member].
- MoCrySEn 2013 ‒ Regensburg, Germany, September 2013 [PC member].
- Selected Areas in Cryptography (SAC) 2013 ‒ Vancouver, BC, Canada, August 2013 [PC member].
- CrossFyre 2013 ‒ Leuven, Belgium, June 2013 [Co-organizer].
- Code-based Cryptography Workshop 2013 ‒ Paris-Rocquencourt, France, June 2013 [PC member].
- YACC 2012 ‒ Porquerolles Island, France, September 2012 [PC member].
- CrossFyre 2012 ‒ Eindhoven, the Netherlands, June 2012 [Co-organizer].
- Code-based Cryptography Workshop ‒ Kgs. Lyngby, Denmark, May 2012 [Organizer].
- PKC 2012 ‒ Darmstadt, Germany, May 2012 [PC member].
- PQCrypto 2011 ‒ Taipei, Taiwan, December 2011 [PC member].
- ECRYPT-II Code-based Cryptography Workshop ‒ Eindhoven, the Netherlands, May 2011 [Co-organizer].
- CrossFyre 2011 ‒ Darmstadt, Germany, April 2011 [Co-organizer].
Cloud Security Alliance - Key Management in Cloud Services
date: 2020.11.10
I actively contributed to the architecture patterns in the Key Management in Cloud Services Guidance document published by the Cloud Security Alliance Key Management Working group.
Classic McEliece - NIST PQC Round 3 Finalist
date: 2020.07.23
NIST announced yesterday that Classic McEliece is one of the Round-3 Finalists in the Post-Quantum Cryptography Standardization Process.
“As such, NIST selected Classic McEliece as a finalist and believes it could be ready for standardization (should NIST choose to select it) at the end of the third round.”
The full report by NIST can be found here.
The Classic McEliece submission in Round 3 is a merger of the Classic McEliece and NTS-KEM submissions to the previous rounds. The submission builds on code-based cryptography with binary Goppa codes, a proposal that has not been broken for more than 40 years.
Blog post on Cryptography Services for Enterprises
date: 2019.10.21
I wrote a blog post on “How to Make Cryptography Services Work for Your Organization” which was published on the IBM Security Intelligence website. Check it out for some real-world lessons learned.
Architect Certification
date: 2019.10.16
I completed the Level 2 certification as IBM and Open Group Architect in October 2019. This certification is not a one-time sit-down learn-stuff-by-heart and forget-all-again. Instead, I earned the certification by working continuously as architect for multiple years and by demonstrating my achievements to an internal review board at IBM.
I have led several large projects as security architect. My reference projects concerned architectures for smart metering security, cryptography services for financial services, and enterprise security architectures. I followed a series of trainings on architecture, design thinking, consulting and project management. I also specialized not only in security architecture, but also learned how IT is managed for a specific industry: in my case I focused on banks. Further I earned this certification by giving presentations at international conferences and summer schools, by creating reusable assets, and last but not least by mentoring others.
NIST PQCrypto Classic McEliece submission
date: 2018.04.07
Classic McEliece Submission to NIST’s Post-Quantum Standardization together with Daniel J. Bernstein, Tung Chou, Tanja Lange, Ingo von Maurich, Rafael Misoczki, Ruben Niederhagen, Edoardo Persichetti, Peter Schwabe, Nicolas Sendrier, Jakub Szefer, and Wen Wang.
Great to see that my Ph.D. research is relevant for the next crypto standardization, i.e., the parameters in the 2008 paper Attacking and defending the McEliece cryptosystem are still holding up.
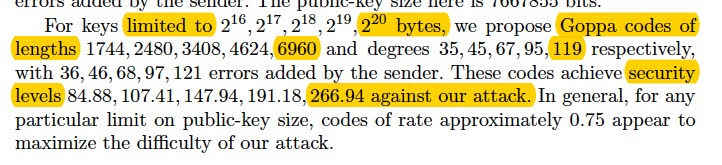
Now included as the IND-CCA2 KEM parameters for mceliece6960119:
m = 13, n = 6960, t = 119, l = 256.
Moreover, more PQCrypto code-based crypto submissions also used my complexity computations to determine the security level of their proposals.
Enterprise Key and Certificate Management
date: 2018.01.09
I gave a lecture at the ECRYPT winter school in Zurich, Switzerland on how large enterprises manage cryptographic keys and public-key certificates.
ECRYPT-CSA School on Societal Aspects of Cryptology and on Business and Innovation in Crypto, 7-9 January 2018,Zurich, Switzerland.
One of the goals was to bridge the gap between industry and academia. I.e., answering the question: how long will it take to get pqcrypto research into practice in a large enterprise environment.
Blog post: GDPR Readiness
date: 2017.03.24
I published an IBM Blog post: What to expect from the GDPR readiness assessment.
Crypto Workshop Girl Tech Fest Brussels
date: 2016.05.04
Together with my IBM Belgium colleagues I organized a crypto workshop for 10-14 year old girls at the Digital Muse Girl Tech Fest in Brussels on Saturday April 30, 2016. We ran 4 workshops where the girls learned how to make and break ciphers - all toy examples of course. Still, lots of fun and great to see that girls enjoy math and crypto!

Dagstuhl Seminar 16032
date: 2016.01.16
Privacy and Security in Smart Energy Grids January 17‒20, 2016 Dagstuhl, Germany Scientific organization together with George Danezis, Stefan Katzenbeisser, and Bart Preneel
Best Paper ARES 2015
date: 2015.08.26
Klaus Kursawe and I won the ARES 2015 Best Paper Award for our paper Structural Weaknesses in the Open Smart Grid Protocol. eprint
FP7 project SEGRID
date: 2015.04.30
While working for ENCS I was one of the researchers on the FP7 project SeGRID (Security for Smart Electricity GRIDs ). I contributed in particular to the deliverables.
D1.1 – Architecture and design for use cases. html
D1.3 – First report on Security & privacy goals. html
Project website: https://segrid.eu/
Austria Smart Meter Security Requirements
date: 2015.03.30
At ENCS I co-wrote the Smart Meter Requirements for Austria’s End-to-End Secure Smart Metering architecture published by Oesterreichs Energie. We wrote the original in German, then added an English translation later. The documents were made available to the public: https://oesterreichsenergie.at/sicherheitsanforderungen-fuer-smart-meter.html
Visiting MSR
date: 2013.02.05
I am visiting the Cryptography Research Group at Microsoft Research in Redmond from February 4 to April 26, 2013. Thanks to Kristin Lauter and Michael Naehrig for inviting me.
Decoding Wild Goppa Codes
date: 2012-10.12
A simple Python script to decode wild Goppa codes. The algorithm is described in detail in the article Wild McEliece.
See here: https://github.com/christianepeters/wild
Postdoc at UIC
date: 2012.10.12
Thanks to Dan Bernstein and NIST for employing me for the period of three months as research associate in the Computer Science Department at the University of Illinois at Chicago.
Also a big thanks to Jon Solworth for giving me asylum in the RITES lab.
Lorentz Center Workshop
date: 2012.10.12
Post-Quantum Cryptography and Quantum Algorithms November 5‒9, 2012 Leiden, the Netherlands Scientific organizers: Tanja Lange, Michele Mosca, and Christiane Peters
Wiki page containing the program, contributed talks, working groups:
https://wiki.pqcrypto.org/mediawiki/index.php/Main_Page
Code-based Cryptography Workshop May 2012
date: 2012.10.12
I organized the Code-based Cryptography Workshop in 2012: May 9-11 at the Technical University of Denmark.
FTP grant
Fall 2011
On September 1, 2011 I started as a postdoc in the Math department at the Technical University of Denmark. The position is funded by a Technology and Production Sciences (FTP) grant by the Danish Council for Independent Research under grant number 11-105325; awarded 1,622,015 DKK for the purpose of conducting research on “Code-based Cryptography”.
Rubicon Award
Summer 2011
Rubicon Award 2011 by the Netherlands Organization for Scientific Research (NWO); awarded 163,763 Euro for the purpose of conducting research on “Code-based Cryptography”; grant money declined because in conflict with FTP grant.
Official announcements in English and Nederlands.
Code-based Cryptography Workshop May 2011
May 2011
Together with Tanja Lange I co-organized the Code-based Cryptography Workshop: May 11-12, 2011 at Technische Universiteit Eindhoven, The Netherlands.
http://www.win.tue.nl/cccc/cbc/
Dissertation
May 2011
In May 2011, I completed my Ph.D. studies at the Technische Universiteit Eindhoven in the Coding and Cryptology Group under the supervision of Tanja Lange and Daniel J. Bernstein.
- Ph.D. thesis: Curves, Codes, and Cryptography. Technische Universiteit Eindhoven. The Netherlands, 2011. pdf bibtex statements
Iteration count for ISDFq attack
Summer 2010
My paper Information-set decoding for linear codes over Fq presents a new algorithm for decoding linear codes over arbitrary finite fields Fq.
The repository https://github.com/christianepeters/isdfq contains a PARI/GP file for a crude operation count as well as a precise iteration count on the basis of a Markov-chain computation. The implementation is written in C and uses the MPFI library. Details on how to use the implementation can be found here.
Iteration count for attack on the original McEliece parameters
Summer 2009
Iteration count of the improved variant of Stern’s algorithm for binary linear codes by Daniel J. Bernstein, Tanja Lange, and myself published at PQCrypto 2008.
Compute the iteration counts for our attack on the McEliece cryptosystem using the type-3 Markov-chain analysis.
https://github.com/christianepeters/isdf2
The implementation is written in C and uses the MPFI library. Note that you might need to increase the level of precision if you consider codes of length greater than 1024. Change the line
int prec = 150;
to something more convenient.
Google Anita Borg Scholarship
June 2009
Awarded to twenty-one selected female Ph.D. and Master students from Europe for excellence performance in computing and technology; I got 5,000 Euro. :-)
http://googleblog.blogspot.com/2009/05/announcing-2009-anita-borg-scholars-and.html
In June 2009 I went together with the other award winners to the Google Europe Anita Borg Scholarship Retreat in Zürich, Switzerland.
SHA-2 will soon retire
Summer 2009
A brief look at the 56 SHA-3 submissions. Joint “talk” by Michael Naehrig, Peter Schwabe, and myself during the rump session of Eurocrypt 2009. Cologne, Germany. slides lyrics and chords youtube
EECM comic
Spring 2008
EECM: using the elliptic-curve method of integer factorization with Edwards Curves.